https//www.racom.eu/eng/products/m/midge/app/wanbac/index.html
Table of Contents
List of Figures
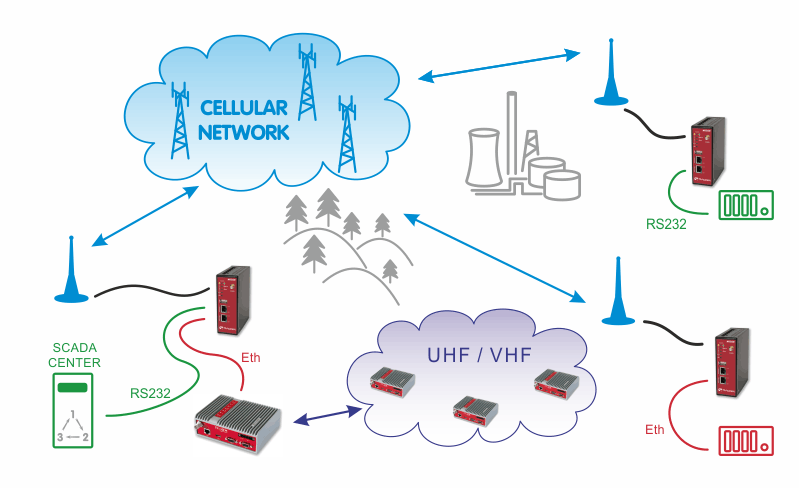
- 1.1. Basic Backup Example
- 1.2. Central M!DGE HOME menu
- 1.3. Central M!DGE LAN1 configuration
- 1.4. Central M!DGE WAN configuration
- 1.5. Mobile interface configuration
- 1.6. IPsec configuration
- 1.7. WAN Link Management
- 1.8. Supervision
- 1.9. WWAN link is UP
- 2.1. MobileIP with VPN tunnel example topology
- 2.2. Server’s Ethernet configuration
- 2.3. Server mobile connection is activated
- 2.4. NTP Configuration
- 2.5. Mobile IP Home agent configuration
- 2.6. Mobile nodes
- 2.7. OpenVPN server, Mobile IP
- 2.8. OpenVPN server – Networking
- 2.9. OpenVPN server – Routes
- 2.10. OpenVPN server – Downloading expert file
- 2.11. Enabling OpenVPN server
- 2.12. OpenVPN server and Mobile IP are running
- 2.13. IPsec – M!DGE configuration
- 2.14. Enabling IPsec – M!DGE
- 2.15. MG102i WAN configuration
- 2.16. MG102i LAN configuration
- 2.17. MG102i Link Management
- 2.18. LAN5 Supervision
- 2.19. WWAN1 Supervision
- 2.20. MG102i NTP configuration
- 2.21. MG102i Mobile IP – Mobile node
- 2.22. MG102i Routing menu
- 2.23. MG102i OpenVPN – Expert file
- 2.24. Enabling OpenVPN – MG102i
- 2.25. OpenVPN and Mobile IP running – MG102i
- 2.26. IPsec configuration – MG102i
- 2.27. Enabling IPsec – MG102i
- 2.28. Ipsec and Mobile IP running – MG102i
- 2.29. Ping probe from MG102i to M!DGE
- 2.30. Using the backup interface